Intego announced on Thursday that it has discovered more strains of the Flashback Trojan horse. The company says that “many Mac users have been infected by this malware,” especially the latest variant, Flashback.G.
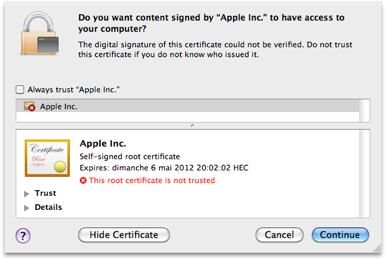
Image courtesy Intego.
Intego describes three unique methods that the Trojan horse uses to infect Macs: It attempts to exploit a pair of Java vulnerabilities in sequence, which the company says allows infection with no further user intervention. Failing those two approaches, resorts to social engineering. In that last case, the applet presents a self-signed digital certificate, falsely claiming that the certificate is “signed by Apple Inc”; if you click Continue, the malware installs itself.
To fall victim to the Flashback Trojan horse, you first need to run software. By definition, Trojan horses disguise themselves as other kinds of software, tricking the user into, say, double-clicking an icon to launch a new download—thereby infecting themselves. Note, however, that if you’re still running Snow Leopard and your Java installation isn’t current, a maliciously-coded webpage could cause the malware to install without further intervention on your part, depending on your browser’s security settings.
According to Intego, the latest Flashback.G variant can inject code into Web browsers and other applications that connect to the Internet, often causing them to crash. It attempts to sniff out usernames and passwords that you enter into many popular sites (like banking sites, Google, PayPal, and others), presumably so that the malfeasants behind the software can exploit that information in other nefarious ways.
As part of its installation process, the malware puts an invisible file in the /Users/Shared/ folder; that file’s name is variable, but it uses a .so extension. Other files the malware creates include/Users/Shared/.svcdmp, ~/.MACOSX/environment.plist, and ~/Library/Logs/vmLog. It also places a Java applet in ~/Library/Caches.
You won’t be surprised to learn that Intego’s own VirusBarrier X6 software can detect Flashback if it’s installed, and even prevent it from installing in the first place.
If you suspect you’ve already been infected, you can check by launching Terminal (in /Applications/Utilities/) and pasting in the code below, and pressing Return:
ls /Users/Shared/.*.soIf the response you see in Terminal includes “No such file or directory,” you’re in the clear. If you instead see a list of one or more files with a .so extension and no “no such file” declaration, you may well have fallen victim to the malware.
If you do find that you’re infected, removing the files referenced above or installing antivirus software like Intego's should remove any traces of Flashback.


